This page covers the SAML 2.0 authentication requests and response sequence that Azure Active Directory (Azure AD) supports for Single Sign-On (SSO) on the Brand Toolbox application.
Contents
- Authenticate Azure AD apps and services
- Azure Enterprise application claims
- Mapping Brand Toolbox groups to Azure AD group/identity names
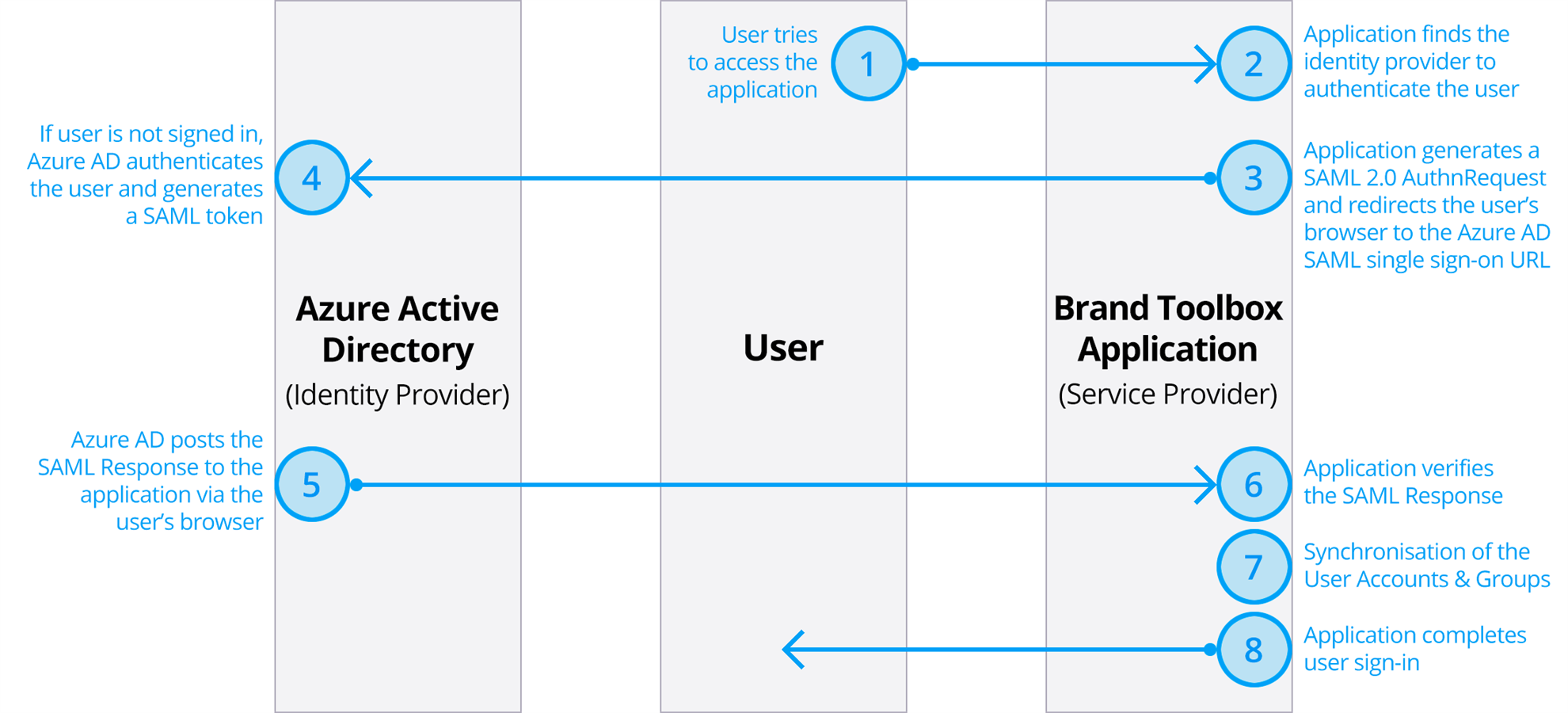
The protocol diagram below describes the Single Sign-On sequence:
The Brand Toolbox Application (the Service Provider) uses an HTTP Redirect binding to pass an AuthnRequest (authentication request) element to Azure AD (the Identity Provider).
Azure AD then uses an HTTP post binding to post a Response element to the Brand Toolbox Application.
Following are the claims that should be mapped (in an Azure Enterprise SAML-based application) to the Brand Toolbox application’s property names:
Required claim
Note that the ‘Unique User Identifier’ element maps to both the username and email.
| Brand Toolbox property name | Claim name | Value |
|
Login and |
Unique User Identifier (Name ID) |
user.userprincipalname [nameid-format:emailAddress] |
Additional claims
| Brand Toolbox property name | Claim name | Value |
|
Full name |
http://schemas.xmlsoap.org/ws/2005/05/identity/claims/name |
user.displayname |
|
First name |
http://schemas.xmlsoap.org/ws/2005/05/identity/claims/givenname |
user.givenname |
|
Last name |
http://schemas.xmlsoap.org/ws/2005/05/identity/claims/surname |
user.surname |
|
|
http://schemas.xmlsoap.org/ws/2005/05/identity/claims/emailaddress |
user.mail |
|
Member Group |
http://schemas.microsoft.com/ws/2008/06/identity/claims/role Custom claim. In “Attributes & Claims”, add by clicking “Add a group claim” and configure with the following Group Claims:
|
user.groups [All] or user.groups [ApplicationGroup] |
|
Company name |
companyname
|
user.companyname |
|
Department |
department
|
user.department |
|
Job title |
jobtitle
|
user.jobtitle |
|
Contact phone number |
telephonenumber
|
user.telephonenumber |
Following is an example of the configured Member Groups and User Groups in the Brand Toolbox application:
Frontend ‘Member Groups’
| Brand Toolbox ‘Member’ Group |
Mapped to [clientName] AD integration group name |
|
[clientName] Employees |
AD integration group: Brandtoolbox-read-only^^ Description: All [clientName] Employees^^ Automatic access via Azure AD (SSO) SAML integration. |
|
[clientName] Brand Team Admin |
AD integration group: Brandtoolbox-admin^^ Description: [clientName] Brand Team (Admin)^^ Automatic access via Azure AD (SSO) SAML integration. |
^^ Examples only
Backoffice ‘User Groups’
| Brand Toolbox ‘User’ Group |
Mapped to [clientName] AD integration group name |
|
[clientName] Brand Team Admin |
AD integration group: Brandtoolbox-admin^^ Description: [clientName] Brand Team (Admin)^^ All new backoffice Administrators and Editors must first be invited to become a backoffice ‘User’. Once successfully logged into the backoffice, the User can link their Active Directory account and, thereafter, automatically gain access via Azure AD (SSO) SAML integration. View further information on Creating a new backoffice User with SSO workflow. |
^^ Examples only
Mapping Brand Toolbox groups to Azure AD group/identity names
To map Member Group names to Azure AD group/identity names:
- Go to the Content section and open Settings > Member Groups

- Choose the individual Member Group^
- In the “Integration” tab, enter the Azure AD group/identity name into the “SSO User Group” property...

- Remember to Save and publish.
^ Note that you must map each member group to its relevant Azure Ad group/identity name.
Create a service principal using the Azure portal
The link below contains the instructions on how to create an app id on Azure AD:
Once the Azure AD application has been created, please supply the Brand Toolbox team with the following three values:
- tenantId – Directory (tenant) ID
- appId – App (client) ID
- wtrealm – Identifier (Entity ID), usually the site Url, e.g. “https://clientname.brandtoolbox.com.au”
Note
If required, the “redirectUrl”, e.g. Replay URL (Assertion Consumer Service URL) is usually the same as the “wtrealm” Identifier (Entity ID).
If authenticating with MSAL/Microsoft Graphs, an “appSecret” value must also be provided.
SSO signing certificate
An SSO certificate^, specifically a SAML certificate, is crucial for SAML authentication and single sign-on (SSO). It’s used to verify the authenticity and integrity of the SAML data exchanged between the Identity Provider (IdP) and the Service Provider (SP).
When adding a new application and configuring SAML-based sign‑on, Microsoft Entra ID generates a self‑signed certificate for the application that is valid for three years. When the certificate expires, simply renew it — do not delete it!
Please follow this tutorial to manage certificate creation and renewal for federated SSO:
After creating and saving a new certificate, upload it to the application, and activate it in in the Microsoft Entra admin center. Once activated, the Brand Toolbox IT Team must then restart the Application Pool on IIS to clear out old cached settings.
^ Note: SAML certificates are distinct from SSL/TLS certificates used for securing website communication. SAML certificates are specifically for authenticating SAML data in a federated identity setup.
Developer notes only
SSO/Active Directory (AD) claims
To view the SSO/AD claims that are captured by Brand Toolbox each time a member attempts to access the application, go to Developer > Trace Logs, and select the last log file (a new one is created every day).
Then filter by the following:
Level: DEBUG
Logger: SessionTokenStore
Note that "debug" must be set to "true" in the web.config for these claims to be viewable in the trace logs. Therefore, to view the claims, change the following from "false" to "true":
<compilation defaultLanguage="c#" debug="true"
and change "identity:ShowPII" from "false" to "true":
<add key="identity:ShowPII" value="true" />
Next page: Multi-Factor Authentication
Back to top